Microsoft has recently released conditional access policies in Azure AD Premium / Intune that will allow you to restrict access to SharePoint and OneDrive from non-managed devices. While this feature is still in preview (expected to go GA by the end of the year), I believe it’ll go a long way to helping companies properly control access to potentially confidential data without needing to block access to OneDrive entirely.
Conditional Access Requirements
In order to use Conditional Access features, you require subscriptions in Azure AD Premium and Intune, and First Release needs to be enabled for everyone in your organization – this setting is found in the Office 365 Admin Portal under Settings – Organization Profile on your tenant (will require up to 24 hours for the feature set to be enabled once you switch):

Enabling Conditional Access Policies
These policies can either be configured in the Azure portal under the conditional access blade in Azure AD or Intune.
Configure a SharePoint Browser Restriction Policy
Start by selecting Conditional access, then Policies, and click New policy:

Give the policy a name, and start working through the options blade – first up is the user assignment; either assign the policy to all users, or select the users or groups you want it to apply to:

Next, choose the Cloud apps blade, and select Office 365 SharePoint Online:

Note that you can set both inclusions and exclusions here – so far I’ve only tried including SharePoint Online, as this is what we’re configuring specifically.
Under the Conditions blade, select Client apps, then choose Configure: Yes, and select Browser under client apps:

Since this policy specifically only targets browser access, that’s the only option we want to select here – we’ll need to create a second policy to restrict access to mobile app and desktop clients.
Access controls is set to Grant access without restrictions, but you can see that you can further lock things down on this tab:

The final option to configure is under the Session controls – check the box to Use app enforced restrictions (preview):

Enable the policy if you’re ready to go, and then click Save.
Configure a SharePoint Device Restriction Policy
Next, we’ll need to enable a device restriction policy in order to prevent users from simply getting around these restrictions by using the mobile apps or sync client.
Just like before, click on New policy, and give it a unique name. The first few settings are exactly the same:
- Under users and groups apply to all users (or restrict it to test users as before);
- Under Cloud apps, select Office 365 SharePoint Online;
-
Under Conditions – Client apps, select Mobile apps and desktop clients:

-
The final option to select is the conditions under which access will be granted. If you plan to use several options like I have below, make sure you pay careful attention to whether or not you require ALL or ONE of the selected controls, depending on how restrictive you’d like to be.

Obviously, you’ll want to set this based on your own requirements, but I think having a device either be domain joined, or Intune compliant is a good way to go. This allows you to support a mixture of managed device types – mobile phones for instance, can’t be domain joined, so you’ll need to allow for them to be managed / compliant instead of just domain joined. One caveat to this specific restriction is that devices need to be registered in Intune in order for them to be properly detected as compliant. If a mobile device is not registered in Intune, then access to the SharePoint / OneDrive app will be blocked, as it will neither be compliant or domain joined.
SharePoint Configuration
Once these policies have been created (and First Release enabled on the tenant), the following options can be configured in the SharePoint admin center, under Device Access:
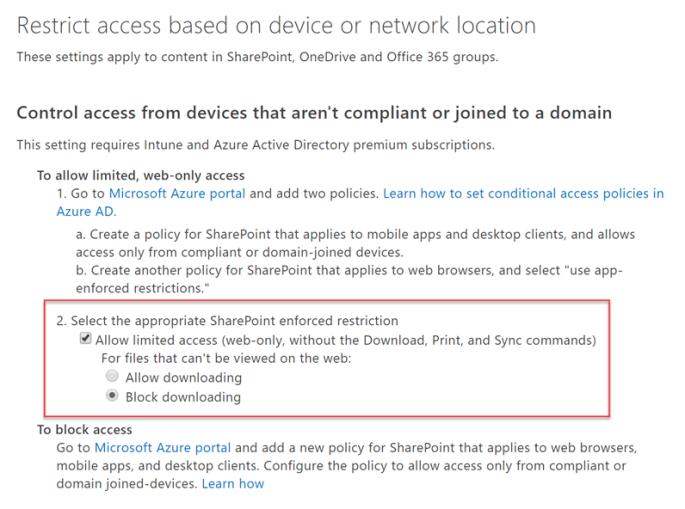
The first option is the two policies we just enabled in Azure AD Premium, and option two actually sets the SharePoint restrictions that we’re looking for.
It’s also important to note that enabling this configuration blocks applications that don’t use modern authentication. I’m still trying to find out what kind of impact this has on Office 2010, but I don’t expect there should be much concern, as Office 2010 doesn’t integrate with SharePoint Online the way Office 2013 and 2016 do.

End User Experience
Once these policies have been applied, users will see the following banner when accessing a SharePoint or OneDrive document library, as well as when access OneNote notebooks in SharePoint Online:

The banner is not displayed while navigating through regular SharePoint sites, it only appears when accessing document libraries, or OneNote notebooks (which are stored in document libraries).
Also, the SharePoint and OneDrive libraries no longer have the New Document, Download or Sync options, and these options also disappear from the document context menu:

Opening up an Office document displays the same banner as above:

The documents are also read only while this is enabled – you don’t have the option to edit the doc, and you can’t copy paste out of this document into another one.
All in all, this is a solid option for locking down access to SharePoint and OneDrive resources, without needing to completely block OneDrive for Business. Users can still have full functionality on trusted machines, but very limited access across the board while on personal or untrusted devices.

